Exploring the complicated realm of information security can feel quite intimidating. Did you know that in 2010, a model known as the “Three Lines of Defense” was introduced to streamline this process? This article will shed light on this powerful framework that assigns clear roles and responsibilities to different parts of an organization, minimizing risk and bolstering security measures.
Ready to level up your approach to cybersecurity? Let’s dive in.
Key Takeaways
- The Three Lines of Defense model assigns clear roles and responsibilities to different parts of an organization, streamlining the information security process.
- In this framework, management serves as the first line of defense, implementing controls to manage risks on a daily basis.
- Risk Management and Compliance form the second line of defense, overseeing risk management processes and ensuring compliance with regulations.
- Internal Audit constitutes the third line of defense, providing independent assurance on controls’ effectiveness and regulatory compliance.
Roles and Responsibilities of the Three Lines of Defense
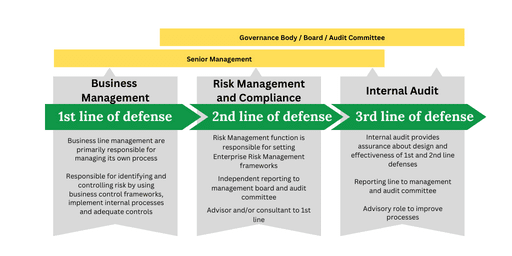
The first line of defense, management, is responsible for implementing and maintaining effective controls to manage risks within the organization. The second line of defense, risk management and compliance, provides oversight and guidance to ensure that risk management processes are in place and followed.
The third line of defense, internal audit, independently assesses the effectiveness of controls and provides assurance to senior management and the board.
First Line of Defense: Business Management
Management takes the mantle as the first line of defense in an organization’s Three Lines of Defense model. They oversee the daily operations and are considered as risk owners, performing hands-on tasks to efficiently manage risks.
This primary layer provides robust protection by setting up control measures, ensuring that potential threats are identified and neutralized promptly. Management’s proactive approach involves identifying uncertainties, implementing mitigation strategies then monitoring for effectiveness.
A well-managed first line is instrumental in fortifying an organization’s defenses against a myriad of cybersecurity issues before they escalate to uncontrollable proportions.
Second Line of Defense: Risk Management and Compliance
In the 3 lines of defense framework, Risk Management and Compliance form the critical second line. This independent control function holds a pivotal role in ensuring risks are effectively managed and controls are implemented properly.
It constantly scans the horizon for emerging risks and regulatory changes that could impact operations or strategies.
At its core, this second line devises robust strategies to mitigate identified risks while adhering to compliance regulations. The goal is not simply reacting to threats but proactively forecasting them, developing appropriate responses in time.
They offer invaluable support to top-tier management by implementing necessary risk controls and maintaining corporate regulatory responsibilities with precision. Through rigorous analysis of both internal policies and external factors, they help shape informed business decisions regarding cyber security practices and overall governance structure within an organization.
Third Line of Defense: Internal Audit
The third line of defense in the 3 lines of defense framework constitutes Internal Audit. This crucial layer within an organization’s security system shoulders a significant load for maintaining information integrity.
It’s their duty to provide objective and independent assurance, assessing how effectively risks were managed by the first two lines of defense and ensuring compliance with regulations.
In essence, their role is akin to that of cyber gatekeepers, vigilantly identifying weaknesses or gaps within risk management processes. They then use this analysis to recommend strategic improvements that can bolster the overall cybersecurity stance.
This makes internal auditors integral components in implementing robust and resilient three lines of defense strategies for information security professionals.
Organization Structure and Activities of the Three Lines of Defense
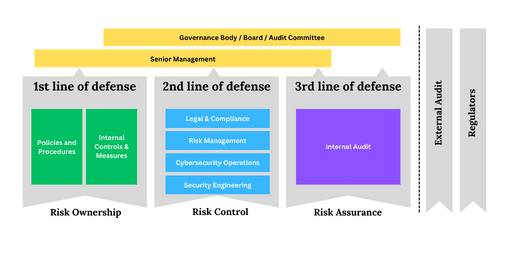
The organization structure of the three lines of defense includes sharing inputs, processing, and outputs to enhance information security. The assurance function within this framework performs various activities to ensure effective risk management and compliance.
Economic allocation of resources is also crucial for the smooth functioning of the three lines model.
Sharing of Inputs, Processing, and Outputs
The Three Lines of Defense model facilitates the sharing of inputs, processing, and outputs in information security. It ensures effective risk management and governance by dividing responsibilities across three lines:
First Line of Defense: Management
- Responsible for day-to-day operations and implementing controls to mitigate risks.
- Inputs: Policies, procedures, and guidelines.
- Processing: Identifying risks, implementing controls, and monitoring effectiveness.
- Outputs: Operational performance reports and risk mitigation plans.
Second Line of Defense: Risk Management and Compliance
- Supports the first line by establishing risk policies and frameworks.
- Inputs: Risk appetite statements and compliance regulations.
- Processing: Assessing risks, designing control frameworks, and monitoring compliance.
- Outputs: Risk assessment reports and compliance status updates.
Third Line of Defense: Internal Audit
- Provides independent assurance on the effectiveness of risk management practices.
- Inputs: Audit plans based on identified risks.
- Processing: Conducting audits to assess control effectiveness and adherence to policies.
- Outputs: Audit findings reports and recommendations for improvement.
Work of the Assurance Function

The work of the Assurance Function is a crucial aspect of the Three Lines of Defense model in information security. This function collaborates with other key functions such as governance, risk management, compliance, and cybersecurity to provide assurance to senior management and the board.
The main objective of the Assurance Function is to assess and evaluate whether controls are effective in managing risks and meeting regulatory requirements. By conducting audits and reviews, they help identify weaknesses in processes or systems that could potentially lead to security breaches or non-compliance issues.
Additionally, the Assurance Function plays a vital role in addressing conflicts of interest, particularly for the Chief Information Security Officer (CISO), ensuring impartiality in assessing information security practices within an organization.
Economic allocation of resources is another important responsibility handled by this function, ensuring that resources are optimally allocated towards managing information security risks.
Economic Allocation of Resources
The economic allocation of resources is a crucial aspect of the three lines of defense model in information security. This refers to how resources, such as budget, personnel, and technology, are distributed among the different functions within an organization’s security framework.
It ensures that adequate resources are allocated to support areas like IT operations and cybersecurity, which are vital for managing information security risk effectively. The COSO three lines of defense model also emphasizes the importance of economic allocation of resources in ensuring the success and sustainability of this framework.
Importance of Cybersecurity in the Three Lines Model
External auditors play a crucial role in ensuring the effectiveness of cybersecurity measures within the three lines of defense framework, holding organizations accountable for protecting sensitive data.
Discover how cyber practices and governance are integrated into this model in order to safeguard against potential threats.
External Auditors
External auditors play a pivotal role in the Three Lines Model, ensuring the importance of cybersecurity. They provide independent assurance and review risk management processes to ensure their effectiveness.
With an objective perspective, external auditors contribute to managing cybersecurity risks and work towards improving cyber risk management maturity while reducing the probability of successful cyber attacks.
Their involvement is crucial for maintaining a robust security framework within organizations operating under the Three Lines Model.
Cybersecurity Practices and Governance
Cybersecurity practices and governance are crucial aspects of the Three Lines of Defense model. They help ensure the protection of valuable information assets, maintain regulatory compliance, and mitigate cybersecurity risks. Here are key components to consider:
- Policies and Procedures: Establishing robust cybersecurity policies and procedures is essential for defining roles, responsibilities, and best practices within an organization.
- Risk Assessment: Conducting regular risk assessments enables proactive identification of potential vulnerabilities and threats, allowing for timely implementation of appropriate safeguards.
- Incident Response Planning: Developing a comprehensive incident response plan helps organizations effectively respond to and recover from cybersecurity incidents, minimizing potential damages.
- Access Management: Implementing strict access controls ensures that only authorized individuals have access to critical systems or sensitive information, reducing the risk of unauthorized access or data breaches.
- Security Awareness Training: Regular training programs educate employees about cybersecurity threats such as phishing attacks, social engineering, and malware, promoting a security-conscious culture within the organization.
- Continuous Monitoring: Employing robust monitoring tools and technologies allows for real-time detection of suspicious activities or anomalies that may indicate a potential cyber attack.
- Compliance with Regulations: Adhering to relevant industry regulations and standards (e.g., GDPR, PCI-DSS) helps organizations meet legal requirements concerning data protection and privacy.
Final Thoughts
In conclusion, the Three Lines of Defense model is a crucial framework for information security professionals. It provides a comprehensive approach to governance, risk management, and compliance.
By delegating cyber risk management responsibilities across different functions and adopting cybersecurity as a risk discipline, organizations can enhance their security posture and effectively address gaps in their security measures.
FAQs
1. What does “3 lines of defense” mean in information security?
In cybersecurity, the 3 lines of defense refer to the model outlining three layers or steps used for risk management and maintaining information security.
2. Can you explain the different levels within these 3 lines of defense?
Yes, the three lines of defense in security management consist of operational management as primary risk owners, a function overseeing risks like an IT department, and an independent assurance body conducting audits.
3. How does this 3 line approach help with risk management?
The 3 lines of defense serve as a systematic method for handling potential digital threats at varied levels thereby managing risks more effectively.
4. Is this concept unique to cybersecurity or can it be applied elsewhere?
While well-suited for issues in cybersecurity, the Three Lines Of Defense Model’s principles are actually broad enough to facilitate risk-management strategies in other sectors too.